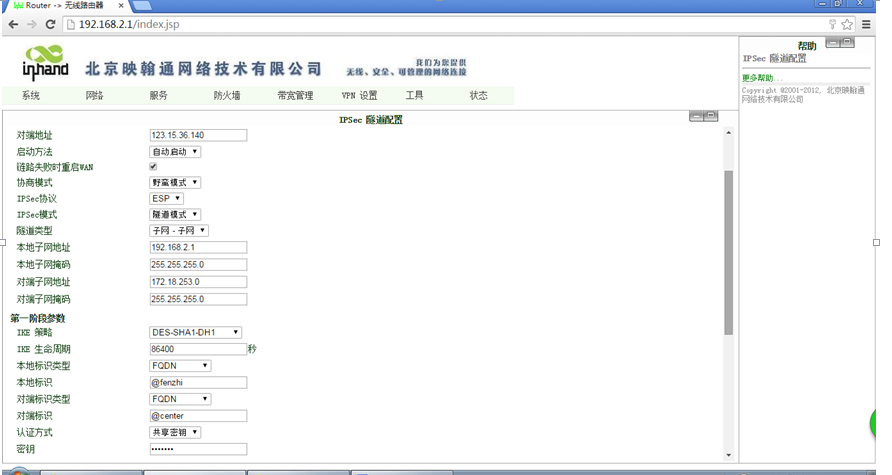
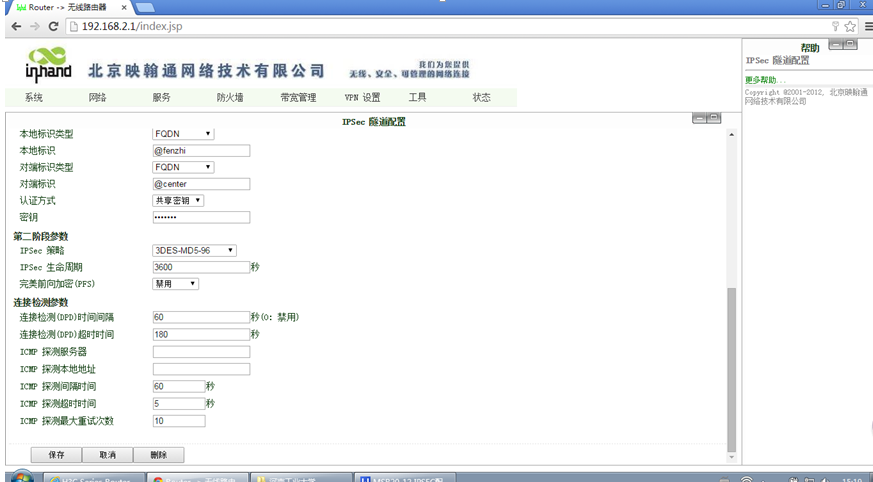
InRouter 与 H3C Router 构建 IPSEC VPN配置指导
<H3CRouter>system-view //进入配置模式
[H3CRouter]local-user admin //添加本地用户
[H3CRouter-luser-cisco]password simple admin //为添加的用户设置密码
[H3CRouter-luser-cisco]service-type web //开启网页配置功能
[H3CRouter-luser-cisco]quit
[H3CRouter]Ethernetinterface Ethernet 0/0 //进入接口配置模式
[H3CRouter-Ethernet0/0] ip address 123.15.36.140 255.255.255.128//配置外网接口地址
[H3CRouter-Ethernet0/0] quit //退出接口配置模式
[H3CRouter-Ethernet0/1] ip address 172.18.253.1 255.255.255.0 //配置内外接口地址
[H3CRouter-Ethernet0/0] quit //退出接口配置模式
[H3CRouter] ip route-static 0.0.0.0 0.0.0.0 123.15.36.129 //配置静态路由
[H3CRouter]acl number 3000 //创建访问控制列表
[H3CRouter-acl-3000]rule 5 permit ip source 172.18.253.0 0.0.0.255//允许内网网段访问公网
[H3CRouter-Ethernet0/0] quit //退出接口配置模式
[H3CRouter]acl number 3001 //创建访问控制列表
[H3CRouter-acl-3001] rule 0 permit ip source 172.18.253.0 0.0.0.255 destination 192.168.0.0 0.0.255.255
rule 5 deny ip //拒绝除内网网段以为的网段访问远端子网
[H3CRouter]Ethernetinterface Ethernet 0/0 //进入接口配置模式
[H3CRouter-Ethernet0/0]nat outbound 3000 //在外网接口上启用ACL 3000
[H3CRouter-Ethernet0/0]quit //退出接口配置模式
[H3CRouter]ike proposal 1 //创建IKE提议,并进入IKE提议视图
[H3CRouter]ike peer fenzhi //创建一个IKE对等体,并进入IKE-Peer视图
[H3CRouter-ike-peer-fenzhi]exchange-mode aggressive //配置IKE第一阶段的协商为野蛮模式
[H3CRouter-ike-peer-fenzhi]proposal 1 //配置IKE对等体引用的IKE安全提议
[H3CRouter-ike-peer-fenzhi]pre-shared-key simple abc123 //配置采用预共享密钥认证时,所使用的预共享密钥
[H3CRouter-ike-peer-fenzhi]id-type name //选择IKE第一阶段的协商过程中使用ID的类型
[H3CRouter-ike-peer-fenzhi]remote-name fenzhi //配置对端安全网关的名字
[H3CRouter-ike-peer-fenzhi]remote-address fenzhi dynamic //配置对端安全网关的IP地址
[H3CRouter-ike-peer-fenzhi]local-address 123.15.36.140 //配置本端安全网关的IP地址
H3CRouter-ike-peer-fenzhi] local-name center //配置本端安全网关的名字
[H3CRouter-ike-peer-fenzhi] nat traversal //配置IKE/IPsec的NAT穿越功能
[H3CRouter-ike-peer-fenzhi]quit
[H3CRouter] ipsec transform-set fenzhi //配置IPsec安全提议fenzhi
[H3CRouter-ipsec-transform-set-tran1] encapsulation-mode tunnel //报文封装形式采用隧道模式
[H3CRouter-ipsec-transform-set-tran1] transform esp // 安全协议采用ESP协议
[H3CRouter-ipsec-transform-set-tran1] esp encryption-algorithm 3des //选择ESP协议采用的加密算法
[H3CRouter-ipsec-transform-set-tran1] esp authentication-algorithm md5 //选择ESP协议采用的认证算法
[H3CRouter-ipsec-transform-set-tran1] quit
[H3CRouter]ipsec policy 983040 1 isakmp //创建一条IPsec安全策略,协商方式为isakmp
[H3CRouter-ipsec-policy-isakmp-use1-10] security acl 3001 //引用访问控制列表3001
[H3CRouter-ipsec-policy-isakmp-use1-10] transform-set fenzhi //引用IPsec安全提议
[H3CRouter-ipsec-policy-isakmp-use1-10] ike-peer fenzhi // 引用IKE对等体
[H3CRouter-ipsec-policy-isakmp-use1-10] quit
[H3CRouter] interface ethernet 0/0 //进入外部接口
[H3CRouter-Ethernet0/1] ipsec policy 983040 //在外部接口上应用IPsec安全策略组
IR600 IPSEC VPN配置